A new VR-glove for realistic sensations of heat and cold

A new VR-glove for realistic sensations of heat and cold

In recent years there have been various approaches to the development of thermal generators in virtual reality technology, which are designed to make the heat and cold felt in the virtual world.
In addition to strange experiments, such as LiquidMask, or dreams of the future, such as brain interfaces, there are prototypes that offer at least some potential. This includes, for example, the technology ThermoReal, which was demonstrated at CES 2020.
KAIST: glove for thermal perception in VR
Researchers from the Korean Institute of science and technology (abbreviated as KAIST) has developed fully self-sufficient thermal glove that allows the user to experience the virtual temperature improved in real-time.
The glove works without external sources or connections.While the movement of the user's hand are transmitted to piezoelectric sensors embedded in a glove of flexible thermoelectric transducers (TED), which replace the previous external thermoelectric device.
Interface card with power supply unit under the wrist that communicates with a computer or VR software over the wireless network. Now if a user touches an object with temperature difference in a virtual environment, is transmitted to the interface Board, which, in turn, controls the sensors in the glove.
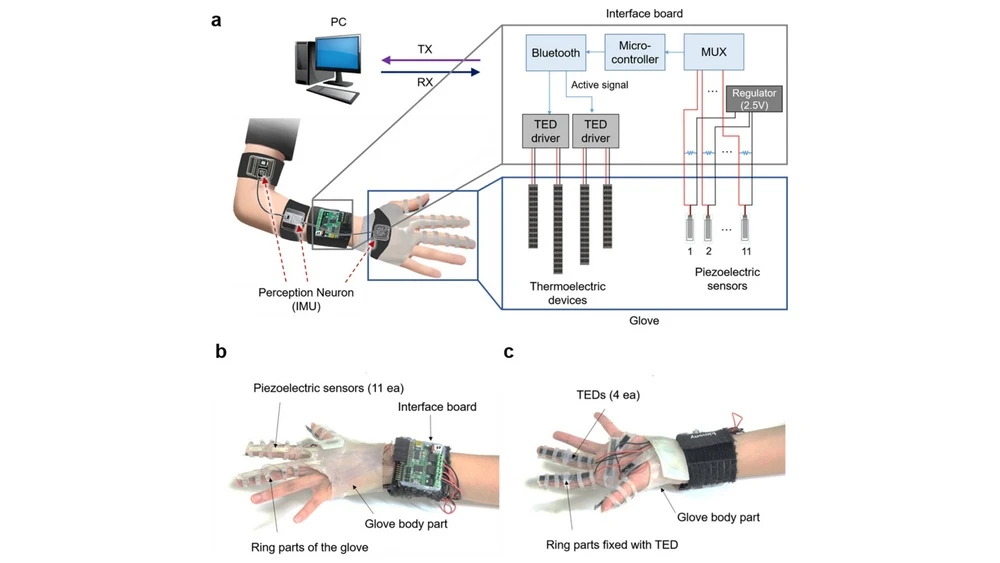
Sensors provoke thermal stimuli on the skin and, thus, transmit simulated temperature. At the same time, the body temperature is measured and taken into account when modeling the temperature. The system works in real time: sensors can simulate the difference of temperatures up to ten degrees in less than half a second.
If tactile gloves for the consumer market?
At the moment, the KAIST researchers have built and tested the glove as a prototype to explore how the temperature really enhances the experience of virtual reality. The realization that the simultaneous measurement of temperature makes the visual stimuli is much more realistic, provided that they are transmitted to the user in real time, is not surprising or innovative.
So far, the glove is just a prototype and can be used for University tests. It must be individually adapted to the respective shape of the user's hands that hardly makes the gloves interesting for the consumer market.
However, as a rule, it is doubtful whether the VR users do not want to wear a glove in addition to the often complicated set up VR to get a little more immersion.
Gloves VR is nothing more than an intermediate stage of the study
In General, the question arises as to whether useful gloves for use with virtual reality. They are suitable only to a limited extent to track their movements or tactile feedback, even if they have a certain potential, for example, Haptic gloves Manus Prime. With hand tracking (e.g., for Oculus Quest) there are much better ways to get your hands in virtual reality.
Source

